Internal Articles
IdP and Outsystems

How to combine IdP and Outsystems for stable solutions
IdP and Outsystems are not directly related however can work together to provide a stable solution for building secure web, mobile and reactive applications.
IdP is an identity provider, using the SAML protocol to connect to external identity providers, that manages and verifies the identities of users. We can incorporate IdP approach to design a Single Sign-On (SSO) login, that allow users have access of multiple applications using their credentials only one. That required an integration with CAS (Central Authentication Service). Some providers are already prepared on IdP to be used quickly like Okta, Azure, ADFS, PingOne, OneLogin, and others.
Otherwise, it is possible configure and create another configuration, and that can happen if, for example, the customer uses their own CAS service.
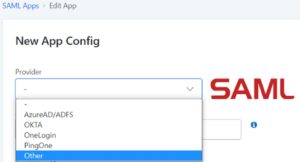
Integrating IdP Connector component required a few steps:
- Download component on the Forge (Outsystems library)
- Create a user to manage IdP, grant role IdP_Administrator on https://your-domain/Users
- Open IdP on the browser and set up the identity provider
- Involves registering your application with IdP and obtaining configurations information like IdP entity ID, Single Sign-On URL, and the certificate.
- Import XML file with SAML metadata from CAS
- Export XML file with SAML metadata to share with external system our configurations
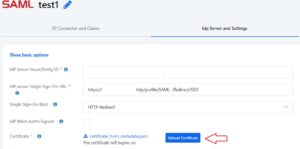
- Upload certificate in IdP (IdP Server and Settings tab)
- Map the IdP attributes (claims) to Outsystems attributes. This is necessary so that Outsystems can understand the user’s identity and other information from the IdP. To build this you can create the mapping between the IdP attributes and the Outsystems user attributes. On IdP you will have some claims created by default, however if you need to create new ones it is possible using “Add new custom claim” link. Claims can refer to a variety of features and capabilities that are related with the authentication and authorization process in the software application.

- To configure the logout process you will need to configure IdP server single logout URL and usually customer give this URL because that will request customer service. To configure that navigate to the IdP Server and Settings and insert the URL (example, https://domain/cas/logout).
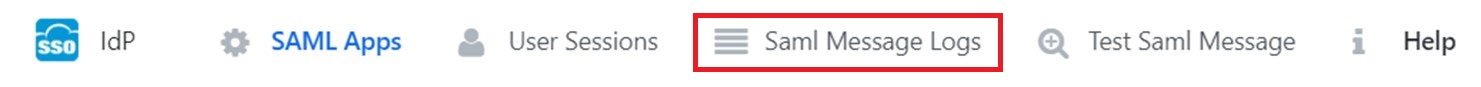
- To test the integration in your application it will helps create a sample app to simulate the login process and that will not impact other features until the IdP login process is not finished. To simulate the process should have a test user created previously in customer side, where CAS service will provide a valid response for IdP. You will be able to track the process using SAML Message Logs.
 In technical perspective integrating an IdP component in Outsystems can be a straightforward process but require some technical expertise and knowledge of this component. On maintenance perspective it will be useful and recognized because IdP is ready to be consumed in multiples applications putting the effort of implementation once time in the development team.Overall, IdP improved user experience by enabling SSO functionality because users can access multiple applications with a single set of credentials. More than that using this component provide benefits for organizations looking to build custom applications quickly and securely, such as GDPR and HIPAA providing audit trails and other features.
In technical perspective integrating an IdP component in Outsystems can be a straightforward process but require some technical expertise and knowledge of this component. On maintenance perspective it will be useful and recognized because IdP is ready to be consumed in multiples applications putting the effort of implementation once time in the development team.Overall, IdP improved user experience by enabling SSO functionality because users can access multiple applications with a single set of credentials. More than that using this component provide benefits for organizations looking to build custom applications quickly and securely, such as GDPR and HIPAA providing audit trails and other features.
 | Sílvia Sendim OutSystems Technical Lead |
Internal Articles
Related Articles